|
有些高端存储设备,硬盘格式化成每个扇区520字节,这种硬盘接到Windows机器时,操作系统启动非常慢,等到系统起来以后,才磁盘管理中能看到硬盘型号等信息。 当用数据恢复工具或者磁盘镜像工具对硬盘进行读取的时候,返回错误信息,硬盘上的任何数据都没办法读,这就是我们常说的“非标硬盘”。 关于非标硬盘的镜像工具,经过多年的摸索,和信工程师张工在几年前联合国内几大高校数据恢复实验室率先研发出windows平台下对520字节硬盘的镜像工具。目前正在把工具产品化。 关于非标硬盘的详细信息,可以参考阅读国外一篇文章,没有精力翻译,感兴趣的可以看看。 |
|
| White Papers | |
| ........................................................................................................... | |
| High Data Integrity on SATA White Paper (August 2005) | |
|
Cost-Effective SATA Solutions Meet the Reliability Demands for Enterprise Storage Applications Introduction The demand for inexpensive, high-capacity storage media is growing at a phenomenal pace. Storage Managers feel the need for reliable and cheaper storage solutions more than ever. Traditionally, the vast majority of Just a Bunch of Disks (JBODs) shipped into enterprise storage applications are based on Fibre Channel (FC) technology. They are built on Fibre Channel Arbitrated Loop (FC-AL) infrastructure, use FC connectivity to Redundant Array of Independent Disks (RAID) controllers and rely on high-priced, dual-ported FC disk drives. These JBODs provide high performance, reliability and availability, but at a high Total Cost of Ownership. Basically, a cost barrier prohibits the use of expensive FC disk drives in all but the most critical enterprise applications. Sierra Logic’s innovative Silicon Storage family of controllers breaks through this cost barrier by enabling the use of lower-cost Serial ATA (SATA) disk drives in integrated storage solutions that leverage Fibre Channel as the connectivity to the RAID controller and between JBODs. Also, the Silicon Storage controllers increase storage system availability, functionality and performance with little modification to existing storage system firmware. The result is a cost-effective, versatile, scalable and transparent solution that justifies moving high performance RAID, Massive Array of Idle Disks (MAID), Network Application Support (NAS) and disk-based backup systems into markets ranging from Small-to-Medium Business to Enterprise applications. SATA disk drives are quickly becoming alternatives to higher-cost FC and SCSI drives for many applications. However, SATA drives by themselves lack enterprise-class data integrity. The Silicon Storage family of controllers with its innovative data protection mechanisms addresses this issue. The focus of this paper is to demonstrate the need for data integrity checks and discuss Sierra Logic solutions that provide enterprise-class data integrity using low cost SATA drives. Need for Data Integrity Checks For a system to be considered for use in the most demanding enterprise storage applications there can be no question about the integrity of the data on that system. The user must be confident that the data corruption is virtually impossible. Serial ATA offers more thorough error-checking and correcting-capabilities on the interface than parallel ATA. The end-to-end integrity of both transferred commands and data can be guaranteed across the serial bus. However, SATA drives may still be susceptible to failures leading to data corruption. The most common cause for data corruption is silent drive errors. Silent drive errors transpire when drives provide bad or incorrect data, but do not provide the host with any error status. In some error cases, the drives erroneously may indicate a good status. An example of a silent drive error is where the drive corrupts data that is requested, but signals a good status to the host. Another example is where the drive provides a wrong sector of data and signals a good status to the host. Because of the “silent” nature of these errors, it is very difficult to pinpoint the origin of the error in a complex storage system. In some cases, only after laborious debug, storage Original Equipment Manufacturers (OEMs) are able to isolate the fault. The need for data integrity checks is emphasized even more if one considers the cost per incident in terms of lost productivity, field support costs and possibly the most damaging aspect, lost customer trust. A number of mechanisms are deployed in FC and SCSI storage systems around the world to ensure data integrity. Sierra Logic's Silicon Storage line of products enables similar protection mechanisms on SATA JBODs and addresses the data integrity issue. By implementing such mechanisms, the primary objective is to improve data integrity and fault isolation and increase interoperability between standardized initiator and target devices. Expanded Sector Size - 520 Byte Algorithm The most common mechanism to ensure data integrity uses expanded sector sizes on the drive medium. In block-based storage, user data is commonly stored in 512-byte blocks. Disk drives can be formatted to fit exactly one block of user data into each sector, or they can be formatted to an expanded sector size, for example 520 bytes per sector (524/528-byte sectors are also used sometimes). In a 520-byte sector, the data integrity mechanism embeds protection information for the 512 bytes of user data into the extra 8 bytes. The 8-byte Protection Information Field (PIF) is interleaved with each user block of data as illustrated below in Figure 1. >  Figure 1 Protection Information Field Appended to the User Data Block (512 Bytes) The protection information is typically vendor-specific, and in most cases, designed to ensure that the data is not corrupted and that the wrong block of data is not inadvertently accessed. Typical contents of PIF are shown below in Figure 2. 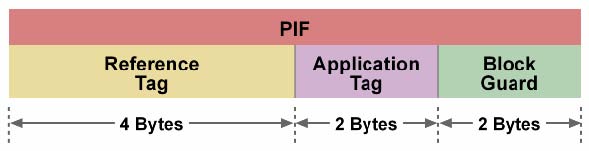 Figure 2 Typical Contents of a Protection Information Field (PIF) As shown in Figure 2, the Protection Information Field is typically composed of three sub-fields, the Reference Tag, the Application Tag and the Block Guard. The Reference Tag contains information associated with a specific data block within some context, such as the lower 4 bytes of the Logical Block Address. During a multi-block data transfer, this field is incremented by one for each successive block. The Application Tag contains additional context information that is held fixed within the context of a given I/O operation. The Block Guard field is computed from the data in the User Data Block. The Tag values in the PIF are excluded from the computation. PIFs allow target devices to receive data with standardized protection information, store the data and associated protection information fields in a proprietary fashion, and then return the data and associated protection information fields in a standardized fashion. Sector Remapping – Translating User Sectors to Media Sectors A native FC JBOD solution using expanded sector sizes requires that the FC Hard Disk Drives (HDDs) be formatted with a media sector size of 520 bytes. A problem arises when trying to employ this algorithm in a SATA JBOD because most currently available SATA HDDs can be formatted only with a media sector size of 512 bytes. The Silicon Storage controllers solve this problem by differentiating user sectors from media sectors. Media sectors are set to 512 bytes, and simultaneously user sectors can be set to 520 bytes (which includes the additional 8 bytes containing protection information that ensures data integrity). The Silicon Storage line of products translate between the 520-byte user sectors and the 512-byte media sectors in a high-performance and space-efficient manner (patent pending). A 250-Gbyte disk drive using 520-byte user sectors delivers 246 Gbytes of useable space. This is identical to the efficiency provided by a 250-Gbyte FC drive formatted with 520-byte media sectors.
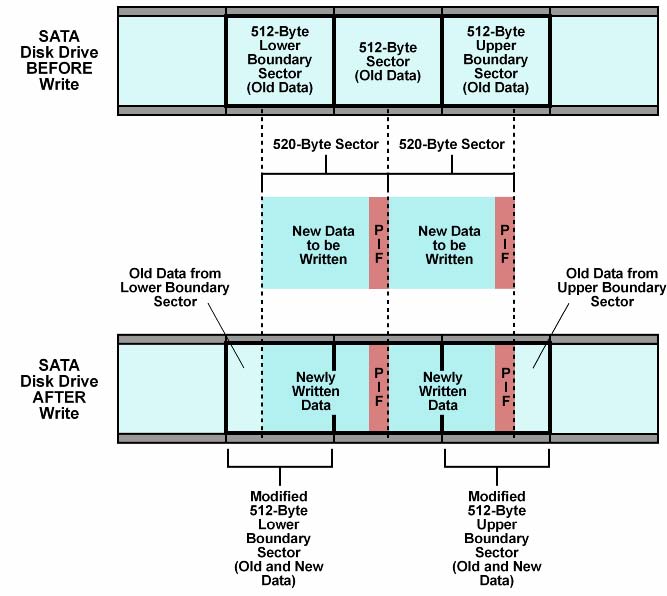
The result is that no data integrity is sacrificed in enterprise storage applications that use low-cost SATA drive technology. Figure 3 depicts how a SATA drive that has media sector size of 512 bytes accommodates 520-byte user sectors. 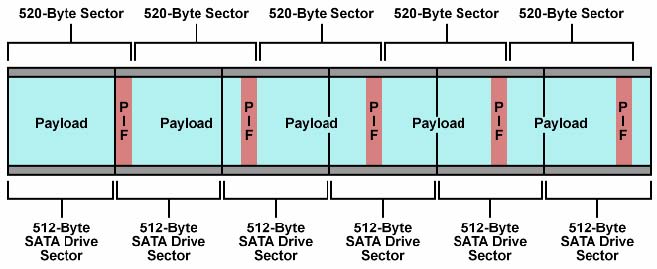 Figure 3 Expanded User Sectors (520 Bytes) in Traditional Media Sectors (512 Bytes) Figure 4 illustrates a typical Disk Write that employs the Read Modified Write Algorithm. In this operation, the 512-Byte Lower Boundary Sector, 512-Byte Middle Sector (this example shows only one such sector, but there may be many such sectors) and 512-Byte Upper Boundary Sector is first read from the SATA drive. The new data that is to be written (two 520-Byte Sectors – which include their respective PIFs) is then placed in the three 512-Byte Sectors, preserving data that was previously valid (e.g. the sections that refer to “Old Data from Lower Boundary Sector” and “Old Data from Upper Boundary Sector”). Finally, the three 512-Byte Sectors (modified Lower Boundary Sector, Middle sector and modified Upper Boundary Sector) are written to the disk drive. Figure 4 shows a simple example that uses only two 520-Byte sectors, but the algorithm scales naturally to any number of sectors. The required calculations to translate user sectors into media sectors are automatically performed by the Silicon Storage controllers. Further, optimization (e.g. based on I/O size, or based on I/O alignment with media sectors) and error handling techniques are employed as well.
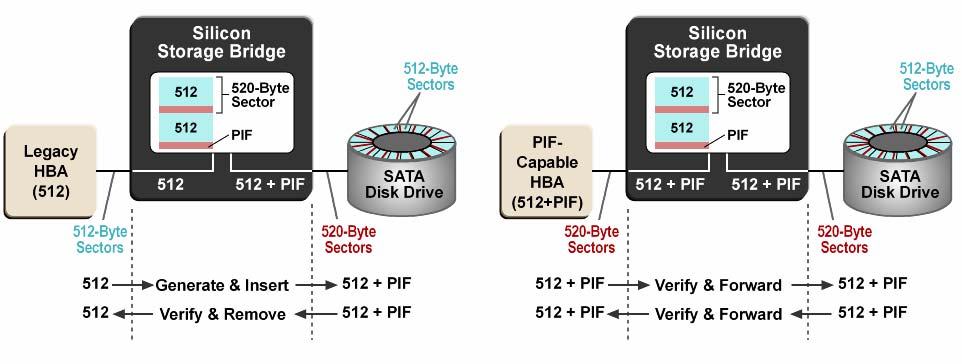
Figure 4 Typical Disk Drive Write that employs the Read Modified Write Algorithm Certain RAID controllers can sometimes optimize the above procedure. If a RAID controller is aware of the native media sector size then it could align the user sector(s) to the media sectors. For example, with 520-byte sectors, the user and media sectors naturally align every 64 sectors. In such a scenario, the Read Modified Write Algorithm is not used. Advanced Data Integrity Options Sierra Logic’s solution is compatible with RAID controllers that support expanded sector sizes and those that do not. In systems where the RAID controller uses expanded sector sizes, the Silicon Storage controllers can verify the standardized protection information fields as data is transferred. On the other hand, in systems where the RAID controller does not support expanded sector sizes (i.e. the data stream does not contain any embedded protection information), the Silicon Storage controllers can generate this vital information and ensure integrity when data is retrieved. Hence, the Silicon Storage controllers can either “Verify” or/and “Generate” PIFs. The Verify/Generate capability could further be applicable to only specific fields within the PIF. For example, some Host Bus Adapters (HBAs) may support only the Reference Tag. In such a scenario, only the Reference Tag is verified, but the Silicon Storage controller may be programmed to Generate the PIF information pertinent to the remaining two fields (Application Tag and Block Guard). This mix and match capability further improves the chances for fault isolation. The block diagrams shown in Figure 5a and 5b depict the capabilities discussed above.
Summary The Silicon Storage controllers provide solutions that enable a new paradigm of enterprise storage systems. With these solutions, IT managers have more cost-effective storage options available to them without sacrificing critical factors such as availability and data integrity. Thanks to industry-leading integration levels, the Silicon Storage controllers demonstrate impressive performance levels using low-cost SATA disk drives and deliver a complete, system-level solution to storage OEMs worldwide. |
|
关于520硬盘的相关信息--数据恢复必备知识 www.jdcok.com/anli/5/1292.html